openfortivpn is used to establish VPN tunnels on linux and compatible with Fortinet VPNs.
Installation
openfortivpn is included in notable linux distributions and can be installed via packet manager:
Fedora:
Ubuntu:
Debian:
Configuration
When starting openfortivpn the following config file is used and should look something like this for the standard vpn tunnel:
#### config file for openfortivpn, see man openfortivpn(1) ### # # host = destination adress VPN-Gateway # port = destination port # realm = realm / name of the vpn tunnel # username = username (CIT-Account) # password = password host = vpngate.frankfurt-university.de port = 443 realm = pub-all username = <CIT-Account> password = <PASSWORD>
Note: realm = pub-all is used for the standard vpn tunnel and is used in most cases but it may differ when using a different tunnel.
Config files for additional tunnels may be created with freely selected names in the same place. NOTE: Depending on the Linux distribution the config files may differ from
/etc/openfortivpn or may be created manually.
The next step is to add the certificate (chain) to the trusted certificates (systemwide).
Fedora
The ca-file includes the certificate chain o GEANT OV RSA CA 4 CA (pem file) and can be downloaded here.
Now execute:
|
Debian/Ubuntu
The ca-file includes the certificate GEANT OV RSA CA 4 CA (pem file) and can be downloaded here. Please note: Debian expects the file to end with .crt. Otherwise it wont process the file and just skipps it.
Now execute:
|
Establish the connection
start the tunnel via
[root@pc ]# openfortivpn
Root privileges (respectively sudo) are needed because a (ppp)-interface is created (see here section Running as root?). When using different tunnels via configuration files the following parameter is used:
[root@pc ]# openfortivpn -c /etc/openfortivpn/<my_tunnel_configfile>
Additional parameters and explanatary notes may be found via the MAN-pages.
NetworkManager-Addon
Openfortivpn can also be used via NetworkManager. The following packets are required and need to be installed:
Fedora:
Ubuntu:
Debian:
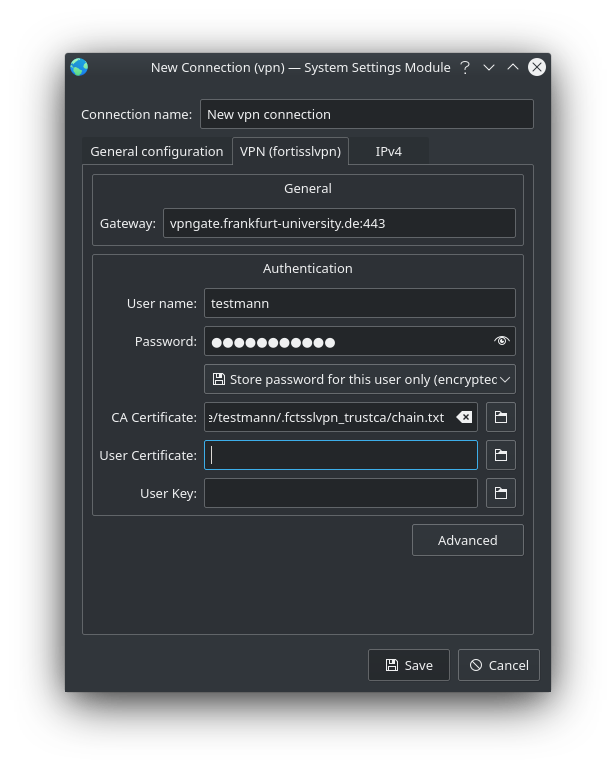
Afterwards a new NetworkManager-profile (type fortisslvpn) can be created.
The configuration should look something like this:
| Option | Value | Description |
|---|---|---|
| Gateway | vpngate.frankfurt-university.de:443 | Gateway address. |
| User name | Your CIT-Account | |
| Password | Your Cit-Account Password |
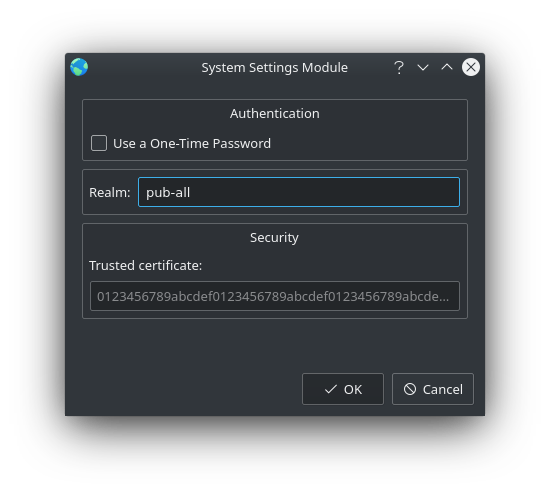
click on "Advanced" to enter the "Realm":
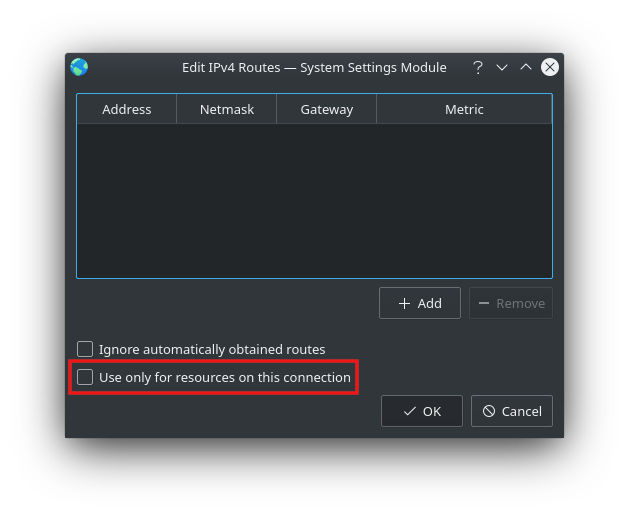
In most cases the realm is pub-all but it may differ when using a different tunnel. Note: Option "Use only for resources on this connection" from IPv4 → Routes must be disabled.
The next step is to add the certificate (chain) to the trusted certificates (systemwide).
Fedora
The ca-file includes the certificate chain o GEANT OV RSA CA 4 CA (pem file) and can be downloaded here.
Now execute:
|
Debian/Ubuntu
The ca-file includes the certificate GEANT OV RSA CA 4 CA (pem file) and can be downloaded here. Please note: Debian expects the file to end with .crt. Otherwise it wont process the file and just skipps it.
Now execute:
|
Afterwards the connection can be established when you click on the corresponding entry in the NetworkManager menu.